Tufin License Usage Reports
Since some versions of the Tufin Orchestration Suite (TOS) licensing and its enforcement is a bit more flexible as in earlier times.
If e.g. 20 devices had been licensed some time ago, adding another device resulted in problems. Now, it's more flexible and you have the possibility to add some devices more than you have licensed. This results in the need of "license usage reports" for Tufin to find out the number of licenses used.
Working with versions up to 24-2, these reports are required, but not really enforced. The license is shown in SecureTrack via Menu > Admin > Administrator > Licenses. At the bottom of the screen License Management the section License Usage is shown.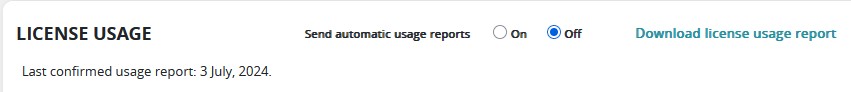
If the option "Send automatic usage reports" is turned on and the system has Internet access, everything is fine. If it's not turned on or connected to the Internet, a manual download of the usage report is recommended. The resulting JSON file is uploaded to the Tufin Portal then.
Starting with 25-1, the license usage reports are enforced. The screen shown above has changed to this: 
It's now necessary to upload the license usage report to the Tufin Portal - and to get the confirmation code that will be sent by E-Mail after the upload. After having uploaded the code shown in the E-Mail to TOS, a message is displayed that the licenses used has been verified. 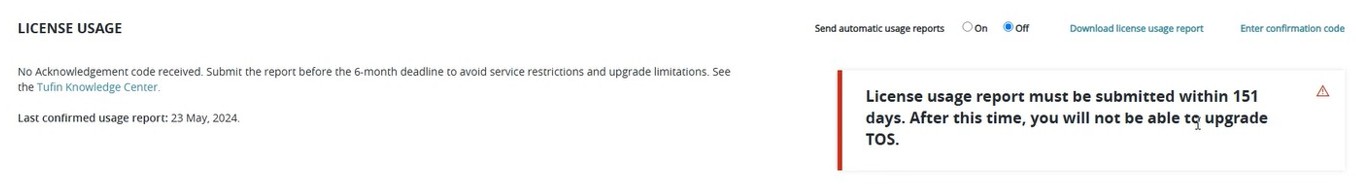
Not following Tufin's guidelines of today, some restrictions regarding the TOS will occur because no Information about Site Usage Monitoring has been supplied:
- Not providing Reports for 6 Months:
There is no possibility to upgrade TOS - Not providing Reports for 12 Months:
No further use of TOS is possible, even if a valid subscription has been purchased
So the flexibility regarding licenses requires a mandatory upload of License Usage Reports to the Tufin Portal now. It's done here via My Account > Available Licenses > Manual Usage Upload - or if TOS is connected to the Internet, via the automatic upload process.